Have you ever thought about what could happen if one of your employees clicked on a fake email link and sensitive customer data got exposed? In just a few hours your business could lose client trust, face unexpected costs and even deal with legal challenges. To protect your company and maintain security, it is essential to take proactive steps to prevent data breaches in business systems.
Every business today relies on digital systems to manage customer details, financial records and internal data. When these systems are not secure, the risk of a breach grows. Common causes of data breaches in business include weak passwords, outdated software and lack of employee training.
Understanding these risks is the first step. By taking practical and proven measures to prevent data breaches in business systems, companies can safeguard sensitive information, maintain client trust and reduce the chances of costly disruptions. In this blog we will explore these risks and share actionable solutions to help businesses build stronger defenses.
If you want expert guidance to secure your systems and protect your data, book a free consultation with TECHOM Systems and get tailored strategies to prevent data breaches in business systems.
Why Preventing Data Breaches Matters For Businesses?
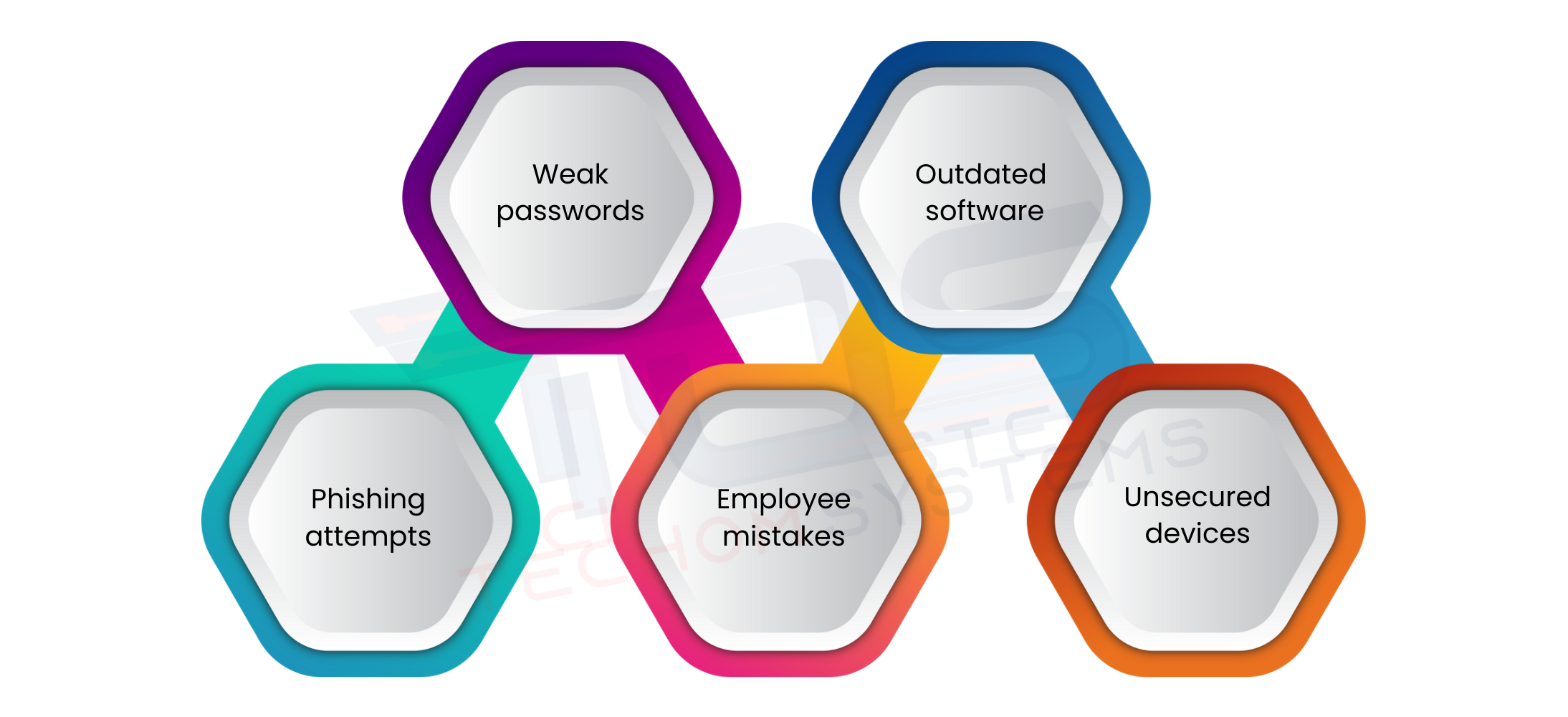
Every business depends on digital systems to store customer information, financial records and internal data. When these systems are not properly secured, the consequences of a data breach can be serious and far reaching. Below are some of the most common causes of data breaches in business that you should be aware of:
- Weak passwords: Employees often use simple or repeated passwords, making it easier for hackers to gain access to business systems. Using strong, unique passwords and multi factor authentication can greatly reduce this risk.
- Outdated software: Software that is not updated regularly can have security vulnerabilities that attackers exploit. Ensuring all systems are updated and patched helps prevent unauthorized access.
- Phishing attempts: Cybercriminals often send fake emails or messages to trick employees into revealing sensitive information. Employee training and awareness programs are essential to recognize and avoid these traps.
- Employee mistakes: Even well-meaning employees can accidentally delete data, misplace devices, or share sensitive information incorrectly. Clear data handling policies and regular training can minimize these errors.
- Unsecured devices or networks: Using personal devices or public Wi-Fi without proper security measures can expose business data. Enforcing secure connections and device policies protects sensitive information.
By understanding these risks early and taking action to prevent data breaches in business systems, companies can protect sensitive information, maintain customer trust and avoid costly disruptions.
Free Tips For You: Cost Reduction Strategies In Business With IT Health Checkup
8 Ways To Prevent Data Breaches In Business Systems
Preventing data breaches in business systems is no longer optional. Every day, businesses rely on digital systems to store sensitive information such as customer details, financial records and internal communications. A single mistake can lead to serious consequences. Below are practical and effective steps to help your business stay protected:
1. Strengthen Authentication
Weak passwords are one of the easiest ways hackers gain access to business systems. Encourage your employees to create strong, unique passwords and set up multi factor authentication wherever possible. This extra layer of security makes it significantly harder for attackers to break into your systems and helps prevent data breaches in business systems from the very first step.
2. Use IT Audit Services
Even the most secure systems can have hidden vulnerabilities. Regular IT audits help identify weak points in your network, applications and hardware. With IT audit services, businesses can quickly spot potential risks, take corrective measures and ensure their systems are always protected before a breach occurs.
3. Encrypt Business Data
Encryption turns sensitive data into unreadable code for anyone without authorization. Even if a hacker manages to access your files, encrypted information remains safe. Encrypting business data is a critical step to ensure that confidential information such as customer records and financial documents always remain protected.
4. Train Employees On Security Awareness
Most data breaches occur because of human error. Employees may unknowingly click on phishing emails or download unsafe files. Regular training sessions on security awareness teach staff to recognize suspicious activity, practice safe online behavior and become the first line of defense against cyber threats.
5. Keep Software Updated
Hackers often target outdated software with known vulnerabilities. By keeping all systems, applications and operating software up to date, businesses can close security gaps before attackers exploit them. Regular updates and patches are a simple yet powerful way to prevent data breaches in business systems.
6. Secure Cloud Storage
Many companies now rely on cloud storage for convenience, but unsecured cloud accounts can be a major vulnerability. Always choose providers that follow strict security protocols, enforce strong access controls and continuously monitor storage systems. These measures help reduce risk of data leaks in business and ensure that sensitive files stay secure.
7. Create Backup and Recovery Plans
Even with the best preventive measures, incidents can happen. Having regular backups ensures that your business can quickly restore lost or compromised data. Test your recovery plans frequently to make sure they work as intended, so a breach or system failure does not disrupt operations or damage client trust.
8. Partner With IT Consulting Services
Professional IT consulting services offer expertise, monitoring and tailored strategies that go beyond standard security measures. Partnering with TECHOM Systems helps reduce risk of data leaks in business, provides ongoing support and ensures your systems are prepared to handle evolving cyber threats.
Worried about what could happen if your business systems were hacked tomorrow? Book a free consultation with TECHOM Systems and get expert strategies to prevent data breaches in business systems before it is too late.
Best Practices For Business Data Security
Protecting business data is about smart processes and consistent habits, not just technology. The table below highlights practical steps your team can take to keep sensitive information safe and prevent data breaches in business systems:
| Best Practice | How To Implement | Why It Matters |
|---|---|---|
| Access Control Management | Give employees access only to the systems and information they need. Review permissions regularly. | Helps prevent accidental or intentional leaks and keeps sensitive data in safe hands. |
| Regular Security Monitoring | Use tools to watch for unusual activity in your network or applications. | Spots threats early so you can stop problems before they become serious. |
| Strong Device Security | Make sure all company devices have antivirus, firewalls and proper security settings. | Protects laptops, phones and other devices from malware or hackers. |
| Data Classification | Organize your data by sensitivity and apply extra protection to your most important files. | Protect your most sensitive data so it stays secure every day. |
| Incident Response Plan | Create a clear process for handling security issues quickly and efficiently. | Reduces downtime and limits damage if something goes wrong. |
| Vendor Security Assessment | Check that third-party partners follow strong security standards. | Prevents breaches from entering through third-party systems. |
| Network Segmentation | Divide your network into separate sections with different security levels. | Keeps hackers from moving easily through your systems if one part is compromised. |
| Regular Data Audits | Periodically review what data you store, why you store it and how it is protected. | Keeps unnecessary sensitive data from piling up and lowers the risk of leaks. |
Following these best practices helps your business stay ahead of potential threats, safeguard sensitive information and maintain client trust every day. Using this table as a reference makes it easier for your team to stay proactive and vigilant in preventing data breaches in business systems.
If you want to know how you can stay aware of risks, then Click Here…
Choose TECHOM Systems For IT Audit Consulting Services
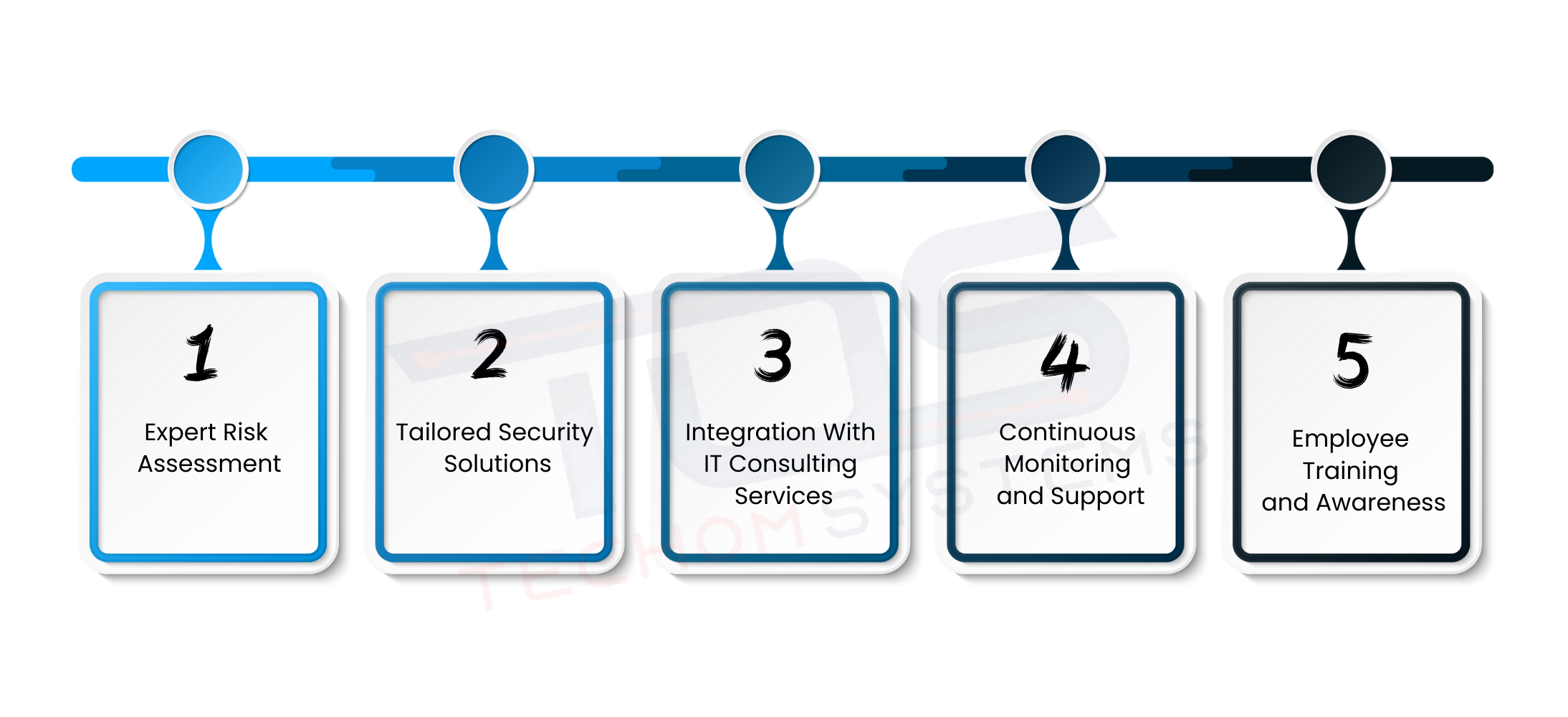
Businesses today rely heavily on digital systems, making it essential to protect sensitive information. Even small gaps in your IT infrastructure can lead to data breaches that affect client trust and business operations. With our IT audit services, we help you reduce the risk of data leaks in business and strengthen overall security. Here are the key reasons to choose TECHOM Systems for expert IT audit consulting services:
- Expert Risk Assessment
We thoroughly evaluate your current IT systems to identify vulnerabilities, ensuring you know where potential weak points exist before they can be exploited. - Tailored Security Solutions
Every business has unique needs. We design customized security measures that fit your environment, including firewalls, access controls and monitoring tools. - Integration With IT Consulting Services
By combining our IT audit services with professional IT consulting, we implement actionable strategies to help prevent data breaches in business systems effectively. - Continuous Monitoring and Support
We provide ongoing monitoring and regular updates to keep your systems secure against evolving threats, reducing the risk of data leaks in business. - Employee Training and Awareness
Human error is a common cause of breaches. We train your employees on safe practices, phishing prevention and secure data handling to strengthen the first line of defense.
Partnering with TECHOM Systems helps your business stay proactive, safeguard critical information and prevent data breaches in business systems with confidence.
How Our IT Audit Process Works
Free Guide For You: Trusted IT Consulting Services in Melbourne
Frequently Asked Questions
#1: How Can Data Breaches Be Prevented?
Ans: Data breaches in business systems can be prevented through regular IT audits, strong access controls, continuous monitoring and employee training. These steps minimize risks and ensure sensitive information stays protected.
#2: What Is The Most Effective Method For Mitigating Data Breaches?
Ans: The most effective method is combining proactive IT audits with ongoing monitoring. This approach quickly identifies vulnerabilities, applies fixes and strengthens defenses against evolving cyber threats.
#3: What Are The Four Actions That Companies Should Perform After A Data Breach?
Ans: Companies should contain the breach, assess the damage, notify affected stakeholders and strengthen security measures. These four steps reduce further risk and rebuild client trust.
#4: What Can Businesses Do To Secure Their Data From Attacks?
Ans: Businesses can secure data by using encryption, updating systems, training employees and relying on trusted providers like TECHOM Systems for expert IT audit consulting services.
Conclusion
In this blog, we discussed how businesses can prevent data breaches in business systems by understanding common risks, implementing practical security measures and leveraging expert support. You learned about the importance of strong authentication, regular IT audits, encryption, employee training, software updates, secure cloud storage, backup plans and partnering with IT consulting services.
By following these strategies, your business can reduce the risk of data leaks in business, protect sensitive information and maintain client trust. Combining smart internal practices with professional support from trusted providers like TECHOM Systems ensures your systems stay secure and ready for future challenges.
Worried About Your Sensitive Business Data Being At Risk?
Contact TECHOM Systems for a free consultation and find out how to prevent data breaches in business systems effectively.
Paige’s 12+ years in tech, cloud solutions and AI innovation have shaped her into a translator of complexity into clarity. She specializes in turning technical strategies and unstructured ideas into actionable, understandable plans for teams and stakeholders. Paige thrives on creating content, workflows and processes that make IT systems accessible, while maintaining accuracy and strategic focus. Her calm, thoughtful approach ensures projects stay on track and teams feel supported, bridging gaps between technology and people. Paige believes clarity in technology is the first step toward meaningful business outcomes.







